Cybersecurity & Training
Lucy Security
Award Winning Security Awareness Training And Phishing
Lucy enables organizations to take on the role of an attacker (phishing simulation) and identify gaps in both the technical infrastructure and security awareness and resolve them through a comprehensive e-learning program.
Why is Lucy's Security Ideal for You?
Lucy Security Training is ideal for businesses because it offers engaging, interactive content that effectively educates employees on cybersecurity risks. Its customizable modules enhance awareness and promote a culture of security, reducing vulnerabilities and helping organizations comply with regulations, ultimately protecting sensitive data and assets.
Having a firewall and antivirus software is important, but employees dealing with e-mail, the Internet, portable data devices, mobile devices, etc. also contribute to security and can be considered the last line of defense.
Award Winning Security Awareness
Training And Phishing
Build A Program
Test
Train
Creating a Safer Digital World through Cybersecurity Training
Creating a Safer Digital World through Cybersecurity Training
Employee Testing
Attack Simulations (e.g., phishing)
Program Building
Customized program based on infrastructure analysis
Employee Training
Integrated LMS
Progress Measurement
Risk and Learning Analysis
Employee Integration
Reporting System (eg. Mail Phish Button)
Build a Program
Understanding the Threat
To understand how a hacker targets an organization, your employees need to know the range of threats facing it. To that end, our mission is to assess the risks in your environment in the most safe and effective way, to ensure that the training delivered is optimized for your organization’s needs. Lucy’s content and attack templates are fully customizable, with relevant training per industry, tech stack, employee group, and local languages.


Preliminary Security Analysis
Interpreting highly technical tests requires a profound expertise in IT security and the know-how of the involved products. It is often possible to improve security by optimizing certain settings. Our security consultants will be happy to support you in the planning and execution of organizational needs.
- Social engineering risk analysis
- Endpoint, mail, and web filter evaluation
- Workforce profile and organizational priorities review
- Osint and darknet investigation
Fully Customized Program
After analyzing the organizational needs and risks, our security consultants will build a customized awareness program. The program will consist of several aspects that will allow you flexibility in the setup and implementation of security awareness training:
- Customized and localized content
- Suspicious activity reporting from users
- Role and results based training
- Industry regulatory standards

Get Started Today with Lucy
Evaluate your organization’s vulnerabilities and threats to build a customized training program for your employees.
Test Your Employees

Prepare for Phishing Attacks with Simulations & Training Courses
Lucy enables organizations to take on the role of an attacker (phishing simulation) and identify gaps in both the technical infrastructure and security awareness and resolve them through a comprehensive e-learning program.
Lucy enables you to simulate the full threat landscape that goes beyond just simple phishing emails
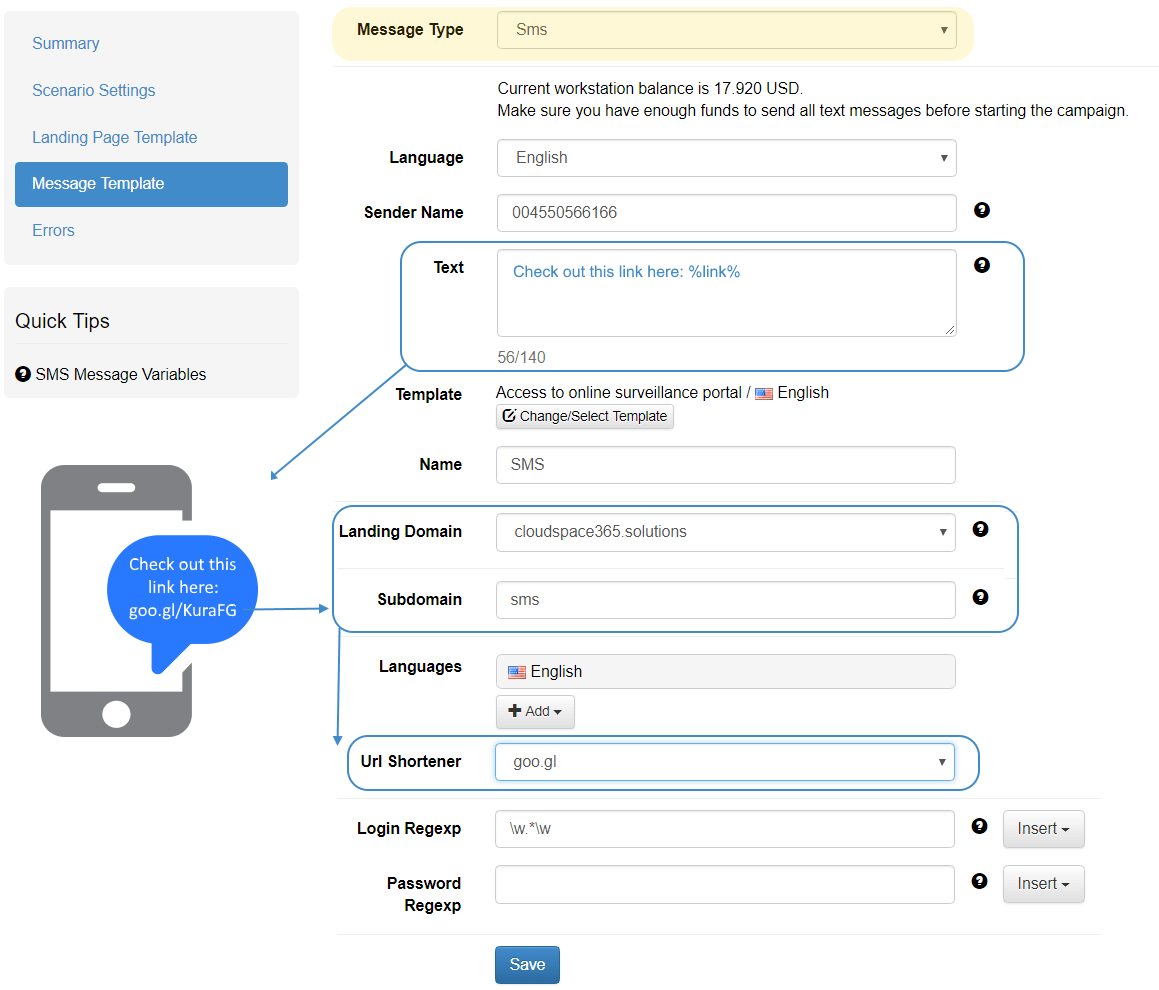
Smishing is, in a sense, “SMS phishing.” When cybercriminals “phish,” they send fraudulent e-mails that seek to trick the recipient into opening a malware-laden attachment or clicking on a malicious link. Smishing simply uses text messages instead of e-mail.
SMiShing
Data entry attacks can include one or more web pages that intercept the input of sensitive information. The available web pages can be easily customized with a LUCY web editor. Additional editing tools allow you to quickly set up functions such as log-in forms, download areas, etc. without HTML knowledge.
Data Entry Attacks
A hyperlink-based campaign will send users an e-mail that contains a randomized tracking URL.
Hyperlink Attacks
LUCY’s flexible redirection functions allow the user to be guided, at the right moment, to the desired areas of attack simulation or training. For example, after entering the first 3 characters of a password in a phishing simulation, the user can be redirected to a special training page about password protection.
Powerful URL Redirection Toolkit
Mixed attacks allow a combination of multiple scenario types (file-based, data entry, etc.) in the same campaign.
Mixed Attacks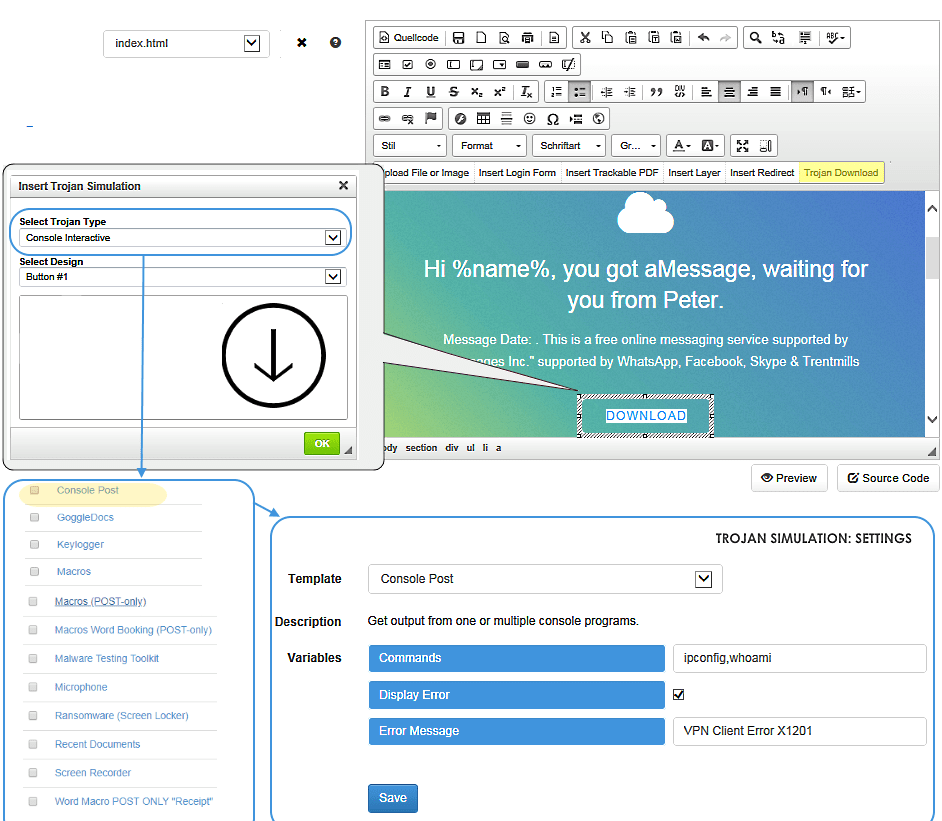
File-based attacks allow the LUCY administrator to integrate different file types (office documents with macros, PDFs, executables, MP3s, etc.) into mail attachments or websites generated on LUCY and to measure their download or execution rate.
File-Based Attacks
This feature makes it possible to send multiple phishing e-mails in each campaign, with the first benign e-mail (the bait) containing nothing malicious and not demanding a reply from the recipient.
Double Barrel Attacks
Java-based attacks allow the LUCY administrator to integrate a trusted applet within the file-based or mixed attack templates provided in LUCY and to measure their execution by the user.
Java-Based Attacks
PDF-based phishing attacks can be simulated with this module. LUCY allows “hiding” executable files as PDF attachments and measuring their execution. Furthermore, dynamic phishing links can be also generated within PDFs.
PDF-Based Attacks
In phishing simulations, false positives must be prevented for log-in fields (e.g., logging with invalid syntax). The company guidelines may also forbid the transmission of sensitive data such as passwords. For this purpose, LUCY provides a flexible input filtering engine that offers a suitable solution for every requirement.
Data Entry Validation Toolkit
LUCY comes with hundreds of predefined attack templates in more than 30 languages in the categories of data entry (templates with a website), file-based (e-mails or websites with a file download), hyperlink (e-mails with a link), mixed (combination of data entry and download), and portable media.
Multilingual Attack Template Library
Attack templates are available for specific industries or divisions.
Sector And Division Specific Templates
Take control of the generated URLs to identify the recipients. Use automated short (< 5 characters) or long URL strings or set individual URLs for each user. The manual URL creation allows you to form links that a user can easily remember. In environments where link clicks are disabled in e-mails, this is a must.
Attack URL Variations
URL shorteners are a relatively new Internet service. As many online social services impose character limitations (e.g., Twitter), these URLs are very practical. URL shorteners, however, can be used by cyber criminals to hide the real target of a link, such as phishing or infected websites. For this reason, LUCY offers the possibility to integrate different shortener services within a phishing or smishing campaign.
URL Shortening
Quickly create highly professional landing pages for your campaigns. Clone existing websites and add additional layers with data entry fields, files for download, and more.
Website Cloner
Level-based phishing training for employees serves to make the risk of social hacking measurable. Scientific analysis should also identify the most important risk factors so that individual training content can be offered automatically.
Level-Based Attacks
The Spear Phish Tailoring works with dynamic variables (gender, time, name, e-mail, links, messages, division, country, etc.) which you can use in landing and message templates.
Spear Phising Simulation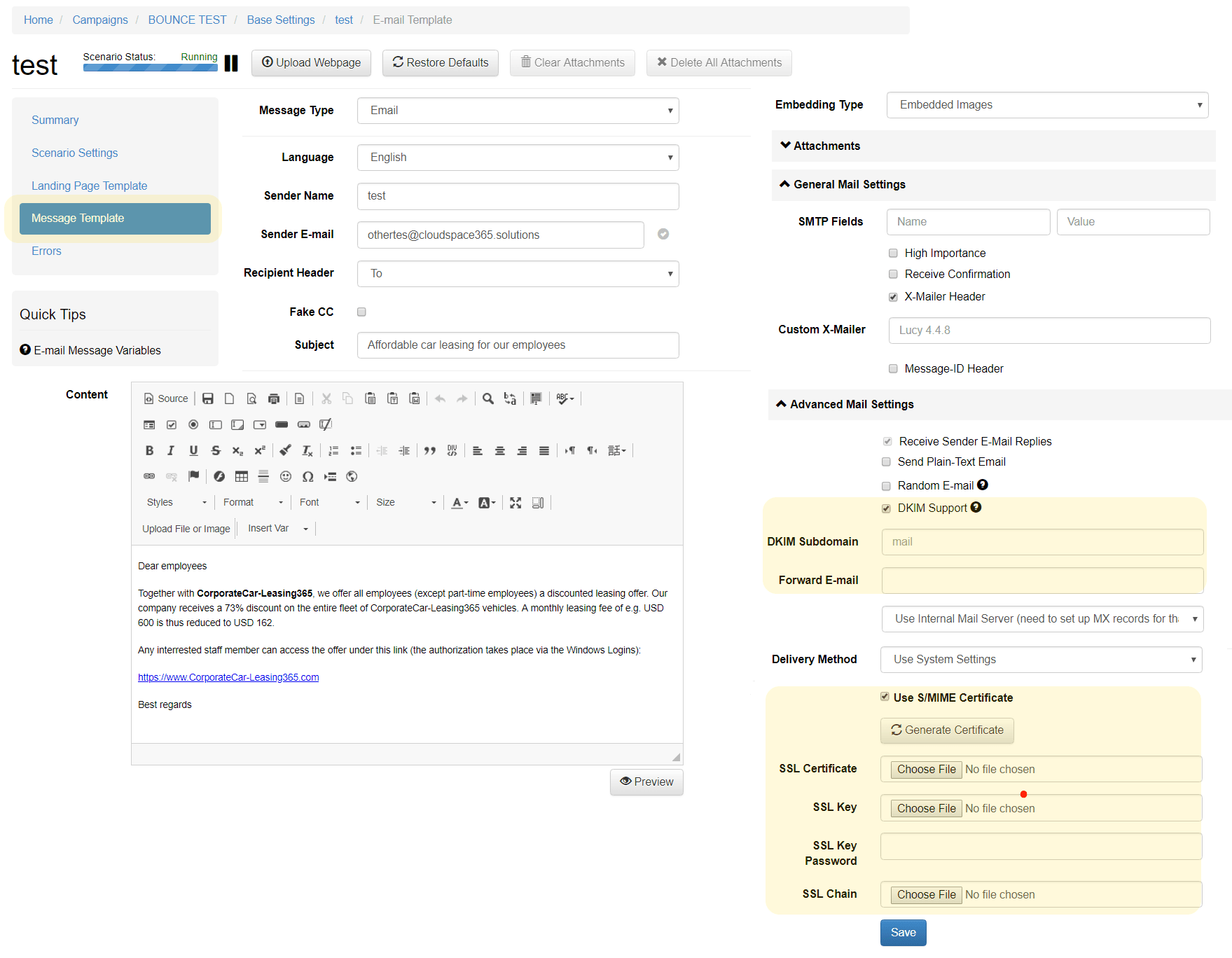
Digital signatures for e-mails: Send signed phishing simulation mails (s/mime). Use DKIM to get a better sender score.
DKIM/S/MIME Support for Phishing e-Mails
Recipients with a better technical understanding could use their browser to call the domain or IP address associated with the randomly generated phishing link. To prevent error messages from appearing or the end user from even coming to the login area of the admin console, you can create generic “homepages” within LUCY for the domains used in the phishing simulation.
Custom Homepage CreationCreate Custom Phishing Templates in Minutes
Make your own phishing templates with our editor and simulate any type of phishing attack. No special technical skills are necessary.

So, How Does Such A Simulated
Phishing Attack Work?
Discuss your requirements
Phishing simulations provide quantifiable results that can be measured. Our available simulations include SMS Phishing, Corporate Phishing (simulated e-mails that appear to come from “inside” your own organization), Board Member Spear Phishing (target a handful of senior individuals in a position of influence) Ransomware Simulation, Personal Phishing (simulations aimed to use well-known brands like Amazon, Apple, eBay, etc.), and many more techniques. These measurements allow improvement to be identified and tracked. The consultative approach our team takes will ensure all phishing simulations and campaigns are bespoke to the threats facing your organization. Prior to the phishing simulation, the needs and objectives are clarified and coordinated with the planned activities. The goal is to define the key elements of the campaign:
Attack or educate first? A simulation test may start with introductory training where employees are educated about e-mail safety and phishing implications. An organization may also set up an anti-phishing e-mail account where employees can readily share their experiences, suspicions, and other requirements concerning cyber threats before starting the simulation.
Frequency of the simulation: Simulation frequency should be adjusted based on perceived threats. User coverage and simulation frequency should be determined in correlation to the perceived risk (e.g., Finance & Payments – 2 themes / X months, senior leadership – 1 theme / X months). High risk functions / departments and individuals handling important roles in the organization should be covered more frequently as part of the simulation.
Length of the simulation: Most phishing simulation tests are usually planned out over a period of 12 months. However, there can be certain ad-hoc campaigns which are situational.
Timing—when to send e-mails? When planning the campaign for each function / department or individual, phishing e-mails should be innitiated with the elements “Day of the week” and “Time of the day.”
Following Up: A phishing simulation campaign may need to be followed up by relevant e-mails from the IT department informing involved employees about the reality of phishing e-mails and what is expected of them in return. If users are repeatedly failing, plan a discussion with them to understand what difficulties they are experiencing and why. Accordingly, arrange for awareness / training sessions for those users.
Consistency with current policies: Once implemented, the process needs to be executed evenly to everyone in scope. Integration into existing information security policies and procedures will also help to give additional importance to the campaign.
Choose the right phishing theme: Please see next section.
Corporate communication: Before initiating the phishing simulation campaign, work out a communication plan about the phishing simulation with the head of function / department. Employees need to be made aware of the new process, what the expectations are, what the consequences of non-compliance include, and when it takes effect.
Targeted group: If the campaign targets a large group of users belonging to the same function / department, they might inform others in the group. Therefore, phishing e-mails should not be forwarded to the entire company as it sparks suspicion. Instead, the process should be organic and must target a small group of select employees at any one time.
Ensure top level commitment: Management support is critical to ensuring that the process is effective. Therefore, higher-tier users need to have a willingness to follow through.
Technical preparations: White-listing of phishing domains, creation of test accounts, mail delivery tests are some of the activities that need to be carefully planned.
 In every phishing simulation activity the theme plays an important part in meeting the end objective of educating users on real threats. To provide a real-world experience and awareness the selected phishing simulation theme should align with an event or context relevant to the targeted individual or group. Here are some points to consider for effective simulation activities:
In every phishing simulation activity the theme plays an important part in meeting the end objective of educating users on real threats. To provide a real-world experience and awareness the selected phishing simulation theme should align with an event or context relevant to the targeted individual or group. Here are some points to consider for effective simulation activities:
Any theme chosen for a phishing simulation should be aligned with business context and perceived risk to the user’s role / function / department.
The selected phishing simulation theme should have relevance to the targeted individual or group.
To achieve better results and learning experience, the complexity of the selected theme should be gradually brought to a higher level.
Starting with a highly complex phishing theme will make many fail and will not achieve the end objective.
Each deceiving element of a phishing e-mail needs to be combined with other tricks typically used by attackers (e.g., look-alike domain with camouflaged hyperlink, spoofed domain with double extension file, etc.).
Each simulation activity should be time bound; contextual themes conducted outside of a defined timeline will lose their value.
The LUCY phishing simulation can be combined with services that will help the company to better assess the risk. Here are a few examples:
Individual trainings: Each employee can be individually trained in advance or directly as a follow-up to the attack simulation. The contents of the training courses can be adapted to the existing company policies. Interactive tests can record the level of knowledge.
Mail and web filter test: It provides technical analysis of the possible entry channels for malware. Which file types can be delivered via e-mail? Which dangerous file types can be downloaded?
Local security test: What is the effective risk if an employee executes a dangerous file type? How well does technical protection work to prevent data leakage?
Analysis of attack potential: Which sensitive employee information can be viewed on the Internet? What do employees communicate via a company e-mail address when on the Internet?
Analysis of security culture: The current security culture is to be recorded and evaluated by means of interviews, surveys, and analyses of existing guidelines.
Darknet analysis: We search the Darknet for existing data leaks and thus show a comprehensive risk picture, which does not only include the inside view.
Fully managed repeating campaigns: Do you prefer recurring campaigns that are completely managed by us? You are welcome to outsource the topic IT Security Awareness completely to us.
Get Started Today With Lucy
Get StartedGet Started Today with Lucy
Evaluate your organization’s vulnerabilities and threats to build a customized training program for your employees.
Train Your Employees

Cybersecurity Awareness Training for Employees
Lucy offers hundreds of interactive, web-based training modules on various security topics. These can be given to employees based on the results of attack simulations, or independently of them.

Train your employees according to their required skills. Measure employee abilities and enable friendly competition between colleagues (gamification). Based on the reputation profiles of each end user, the system can automatically provide them with multiple training sessions. The reputation profiles are based, among other factors, on the user’s behaviour in phishing simulations. This ensures that users who are repeated offenders receive different training content from those who click on an attack simulation for the first time.
Reputation-Based e-Learning
Learning Management System (LMS) functionality: Gives each employee permanent access to a personalized training homepage that features your own courses specifically tailored for them. On this homepage they can view their performance statistics, resume or repeat training, create course certificates, and compare their results with other departments or groups.
End user Training Portal
Certificates of e-Learning can be created and printed out by the recipient either directly within a training or inside the LMS portal.
Awareness Education Diploma
Integrate rich media (video, audio, or other elements that encourage viewers to interact and engage with the content) in your awareness trainings. Use the existing educational videos, adapt them, or add your own rich media.
Rich Media Awareness Training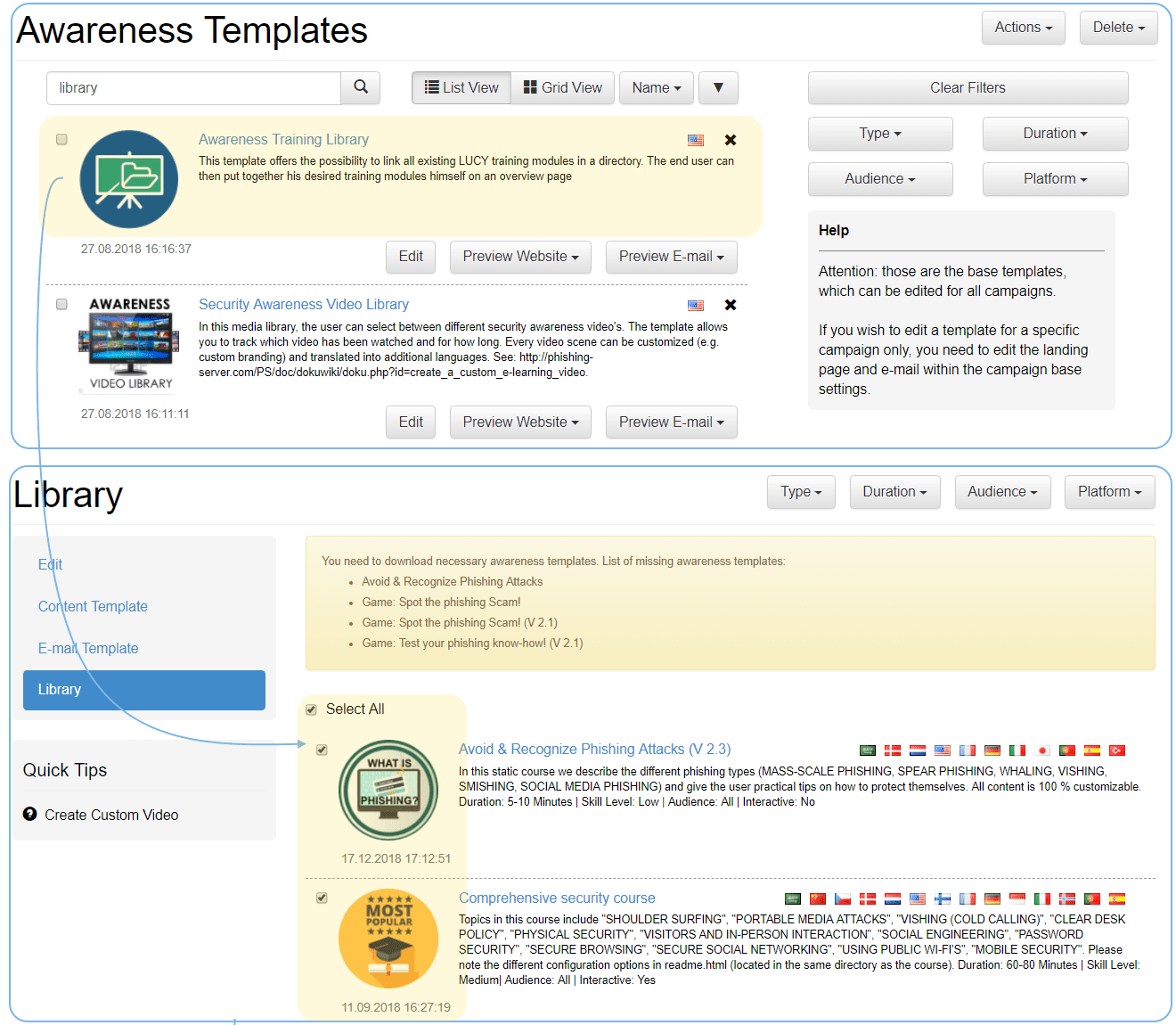
Your employees can access your organization’s training content from an overview page called “training library.” It contains a large selection of LUCY’s regular e-learning templates, which serve as input. The overview page can be sorted by certain topics (video, quiz, test, etc.).
Training Library
Training content can also be published on static pages within LUCY or the intranet, giving the user permanent access to training content, independent of possible attack simulations.
Static Training Support
LUCY is supplied with a series of editable templates (Adobe Photoshop or Illustrator files) for awareness training, such as posters, screensavers, fliers, etc.
Offline Training Support
We have designed microlearning training modules (e.g., 1-minute videos or awareness 1-pagers) that can be tailored to the branding and policy needs of your organization.
Microlearning Modules
Many of LUCY’s built-in modules are available in a mobile-responsive format that gives your users the flexibility to take the training on any type of connected device.
Mobile-Responsive Format
You can export LUCY videos to your own system as well as import your own videos into LUCY.
Video Import/Export
You can also export LUCY’s proven best practice training content to another LMS (Learning Management Solution) with the widely used SCORM interface.
SCORM Import/Export
The implemented dynamic hints allow your administrator to set markers within the attack templates that could indicate to your employees, inside the e-learning material, where the phishing attack may have been detected.
Dynamic Training HintsLearning Methodology
To upskill your employee’s level of knowledge about security, Lucy’s training suite includes both real-life attack samples and cybersecurity training materials. For an effective learning experience, Lucy uses various learning methodologies including microlearning and gamification, leveraging various mediums such as videos, tests, quizzes, and more.

Real-Time Reporting
Our real-time reporting dashboard and automatic monthly reports allow you to measure employee progress, while maintaining full control and visibility of the program. You gain insights that are easy to understand, communicate to stakeholders, and take action on.
Get Started Today with Lucy
Evaluate your organization’s vulnerabilities and threats to build a customized training program for your employees.
Engage Your Employees

Turn your employees into human firewalls
No technological solution can fully address security risks; companies must foster a security-conscious culture. Employees should feel empowered as vital components of the cybersecurity strategy, acting as a “human firewall.” This firewall comprises three key elements: employee education, minimizing human error, and proactively addressing emerging threats. The goal is to enhance user awareness, transforming them into a robust defense against security breaches. Building this firewall involves more than just one-off training; it requires engaging and enjoyable methods to instill secure thinking, preventing humans from becoming the weakest link in organizational security.

End users can report suspicious e-mails with a single click to one or multiple e-mail accounts and have them forwarded to your LUCY incident analysis console.
Report E-mails With A Single Click
Our plugin automatically provides positive behaviour reinforcement by showing gratitude to end users via a custom message defined by your organization.
Positive Behavior Reinforcement
Sometimes users want to know if the received e-mail can be opened safely. The user can optionally use the “deep inspection request” within the local plugin to tell the security team that he wants feedback on the reported e-mail.
Deep Inspection Request
Manage and respond to reported suspicious e-mails using a centralized management console: Lucy analyzer allows an automated inspection of reported messages (header & body).
Incident Analysis
The Incident Autoresponder allows sending an automated notification to the end user providing the results of the e-mail threat analysis. The message text is freely configurable, and the LUCY E-mail Risk Score can also be included, if required.
Incident Automatic Feedback
The behavioural threat mitigator is a revolutionary approach to eliminating e-mail risks. It will support the security admin in shutting down the attack (e.g., sending an automated report to specified abuse team of providers involved in the attack).
Threat Mitigation
Define your own rules for e-mail analysis and risk calculations.
Custom Rule-Based Analysis
LUCY allows an easy customization and a complete white labelling of various plugin functions (displayed icon, feedback messages, ribbon label, transmission protocol, sent header, etc.).
Plugin Customization Options
Using LUCY’s incident REST API automation, we can process reported e-mails and help your security team stop active phishing attacks while in progress.
Third Party Integration
Apply LUCY’s dashboard filters to detect common attack vectors across your organization. Search within all reported e-mails for similar indicators of compromise.
Identify Attacks With Common Patterns
Classify users with an incident reputation score.
Incident User Reputation Profiles
Seamless report and dashboard integration with phishing simulations: identify the users who have behaved exemplarily in a phishing simulation.
Integration With Attack Simulations
Install the Phishing Incident Plugin for Outlook, Gmail, Office365.
Easy InstallationWhat Makes Us Different?
Data Protection
No matter where you install Lucy, privacy is ensured. Lucy complies with the strictest data protection regulations.
Know-How
Our team of former “ethical hackers” covers the entire spectrum of attack methods that go far beyond simple phishing. Attack methods and learning content are constantly updated in Lucy.
Installation
Set up in just a few minutes. You can run Lucy localy on the Intranet, as a cloud-based SaaS solution on all common platforms (Unix, Windows), or on our own dedicated server.
Integration
The Lucy interface package (Domain API, LDAP API, SMTP API, REST API, etc.) supports the administrator and allows a quick integration into the existing infrastructure.
Features
Lucy offers unique features in the areas Test, Assess, Engage, Train, and Report that are only vaguely, or not at all, supported by other companies on the market.
Price
We offer a great value through a variety of offers. From our Core package which includes the critical security awareness, to our Elite package that include all the features and services you need for a world-class security awareness program.
Get Effective Cybersecurity Training
Powerful Phishing Platform + Awareness Officers = World-Class Awareness Program
Enterprise Core
- PLAN FEATURES INCLUDES
- Employee Directory Integration
- Fully Customizable Content
- Realistic Phishing Attacks
- Built-in Email Server
- Real-Time Dashboards and Custom Reports
- Application Security Training
Enterprise Pro
- ALL CORE FEATURES, PLUS:
- In-App Phishing Domain Registration
- Real-Time Event Notification
- Advanced File Based and Smishing Attacks
- Email Report Button
- Compatible with any LMS
Enterprise Elite
- ALL PRO FEATURES, PLUS:
- Multi-Tenant Deployment
- Dedicated Awareness Engineer
- Full Data Anonymization
- VIP Support
- Highest Credit for Services
- On-Prem Deployment Option
Service Catalog
Unique at ThriveDX, we offer dedicated Awareness Engineers, who provide complimentary services to boost your training program. Every license includes a Services Credit, which can be used to purchase services from our extensive catalog.
Managed Awareness Program
Spear Phishing/Vishing
Whaling
Template Translation
Template Customization
Video Customization
Video translations
On-Prem Installation
Compare Plan Features
- Core
- Pro
- Elite
| Core | Pro | Elite | |
| + Setup | |||
Employee Directory Integration
Employee Directory Integration Quickly import employee data for efficient onboarding from Active Directory, Azure, or any other user directory using LDAP.
| |||
Built-in Email Server
Easily launch effective attack simulations using spoofed domains from our built-in server with no integration required.
| |||
Advanced Security Features
To ensure the security of your domain, data, and users, ThriveDX provides all modern security privacy and authentication standards, including Certificate-Based Authentication, DMZ Installation, 2FA/SSO, data anonymity, Hardened VPS, and more.
| |||
Platform Customization
Customize the admin platform and user experience according to your brand.
| |||
Multi-Language Admin Interface
Our admin interface is available in multiple languages including English, German, French, Italian, Portuguese, Spanish, Russian, Turkish, Dutch, and Ukrainian.
| |||
In-App Domain Registration
Easily purchase domains for phishing simulations through ThriveDX's API.
| |||
Security Event Notification
Connect with security information and event management platforms using our global API. Streamline data sharing and analytics for more informed decision-making.
| |||
Multi-Tenant Deployment
Deploy ThriveDX separately for multiple clients and sites as needed with our tailored solution. Know which business units and locations are performing well and are in compliance, and which ones need help.
| |||
On-Prem Deployment
Deploy the platform on-prem for maximum data privacy, guided by our technical team through initial installation and ongoing updates.
| |||
| + Attack Simulations | |||
Real-World Phishing Attacks
Simulate real-world phishing attacks using advanced features including: data entry, double-barrel, spear phishing, and website spoofing.
| |||
File-Based Attacks
Simulate attacks utilizing popular file types, with extensions like DOCX and PDF.
| |||
USB Attacks
Download auto-executable files to a USB drive to test employee awareness.
| |||
Ransomware Attacks
Simulate ransomware attacks through downloadable files or malicious links.
| |||
Smishing Attacks
Execute phishing attacks via SMS to employees’ mobile phones.
| |||
| + Training Content | |||
Extensive Training Library
The content library covers all types of cybersecurity subject matter for any type of industry in different content formats such as video, quizzes, games, and more.
| |||
HTML Content Editor
Easily customize learning material according to your specific security policies and brand needs.
| |||
Localization
Training is available in multiple languages with additional translation services available.
| |||
Microlearning Modules
Provide employees with short learning sessions they can complete on the go.
| |||
Certificate Generator
Celebrate employees’ achievements with a customizable auto-generate certificate.
| |||
Compatible with any LMS
Easily deliver all learning material through your own Learning Management System.
| |||
Employee Training Portal
Provide employees with access to their personal training portal where they can access curated sessions, continue sessions & see results & certificates.
| |||
Performance-Based Training
Monitor employee progress and deliver personalized content based on employee performance and individual risk assessment.
| |||
ThriveDX Application Security Training
(Formally Contra). Get access to select content from our market-leading Application Security Training solution for programmers, which includes:
| |||
| + Reporting | |||
Real-Time Dashboard
Get real-time insights on campaign stats, system status, employee performances, and more.
| |||
User and Group Level Insights
Track user and group level activity and completion rate to get full visibility of employee progress.
| |||
Custom Report Templates
Create customized and automatic reports on training activity and phishing simulation results customized for the needs of any stakeholder (management, compliance, HR..)
| |||
Email Report Button
Allow employees to report suspicious emails with a single click.
| |||
Full Data Anonymization
Maintain employee privacy by exporting information without personal data.
| |||
| + Support | |||
VIP Support
Our VIP support service ensures that customers' tickets receive exclusive attention from our Tier 2 support engineers.
|
Award Winning Security
Awareness Training Platform

Anti-Phishing

Breach & Attack Simulation

Security Education Platform

Cybersecurity Education and Training

Security Education and Platform

Security Training and Educational Programs

Competitive Strategy Leadership

Pitch Your Product Award
Read What Others Think
“What we appreciate most about partnering with Lucy for our Cyber Defense Certificate Program is their commitment to optimizing the training based on current industry needs and trends. With their help, our students can experience a truly hands on program curriculum that helps prepare them well for various cybersecurity roles.”

“It is very important for us to minimize potential cyber risks. In addition to technical security, this includes above all raising the awareness of our associates. With the help of Lucy we show our workforce how each individual can make a contribution to increase security in the company.”

"The Lucy team exhibited exceptional professionalism, responsiveness, and attention to detail throughout our partnership, fostering a strong and positive working relationship. Lucy's proactive problem-solving approach ensured that any challenges or concerns were addressed promptly, further solidifying our trust in their capabilities."

- Related Case Studies


Hackers can use portable media drives to gain access to sensitive information stored on a computer or network. LUCY offers the option to perform portable media attacks where a file template (e.g., executable, archive, office document with macros, etc.) can be stored on a portable media device such as USB, SD card, or CD. The activation (execution) of these individual files can be tracked in LUCY.
Portable Media Attacks